Hacking on the Law’s Side
Yes, you read that right. It is quite possible to hack on the side of the law and this practice is popularly known as ethical hacking and the professionals as ethical hackers. Simply put, ethical hacking is basically getting permission to access an unauthorized computer, application or software, however, this does involve duplicating the malicious strategies of illegal hackers.

What is Ethical hacking-
When hacking is done in the interest of finding threats, prior existing loopholes in the cyber security department and anything else that could be taken advantage of by a malicious hacker, it is known as Ethical Hacking.
The entire world works on cloud storage these days. Millions of documents, trillions of monetary funds, national security files and so many other top-secret documents are stored on computers and clouds. These are what cyber units protect. This is where ethical hacking plays a vital role. Ethical hackers work for governments and organizations to safe-guard their interests.
Importance of Ethical Hacking-
In this advent, where it is said World War III would be found online, the role of ethical hackers increases greatly. Terrorist organizations who fund cybercriminals to penetrate and breach security systems to compromise the national security of a state or nation by injecting malware and viruses is the primary reason for the increase in cyber-crime.
Governments and organizations are challenged with an increase in demand to keep their security systems up and running and most importantly updated and secure. There are new viruses, malware, worms, etc. being created on a daily basis and without anyone to protect computers from these the world will go berserk.
Read More: NFTs and everything you need to know about them
This is where the Ethical Hackers come in.
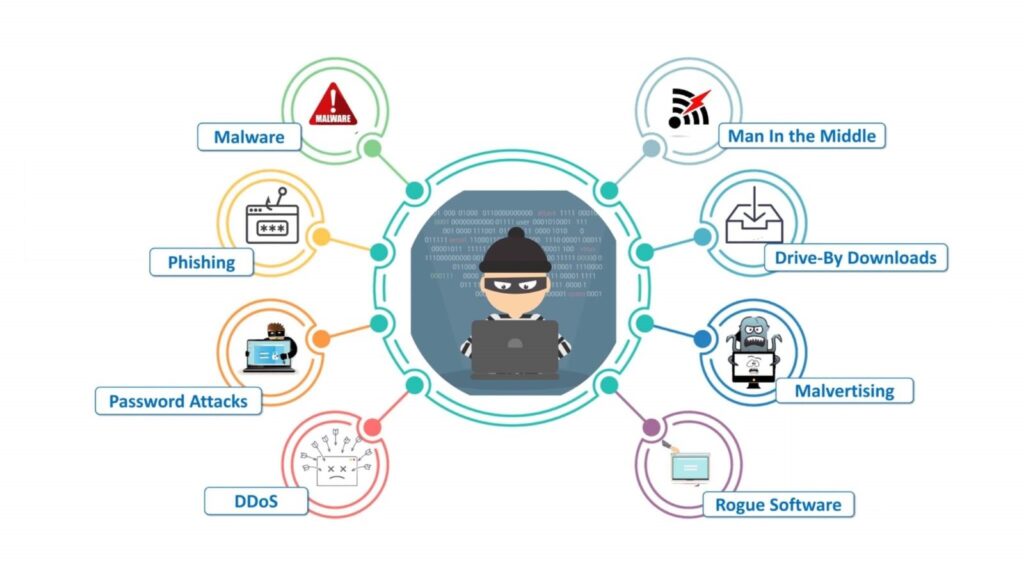
Skills required-
The skills required to become an elite ethical hacker are to have an in-depth knowledge about the different types of networks, systems, programs, codes.
- Programming knowledge- It is an integral part of hacking to know about your programing and what language to use. It is necessary in the field of Application security and Software Development Life Cycle (CDLC).
- Scripting knowledge- This is a requirement for professionals dealing with network-based attacks and host-based attacks.
- Networking skills- This is an important skill to have as most hackers attack from different networks. You should be aware of how many networks there are, how many devices there are present on the network, where the network is coming from and most importantly, what to do if your network is compromised.
- Understanding databases- Databases are most vital as they are the subject to the most attacks by hackers. To have a good understanding of SQL will help you effectively to gather intel and look after operations.
Read more. NFT’s and Everything You Need to know about them.
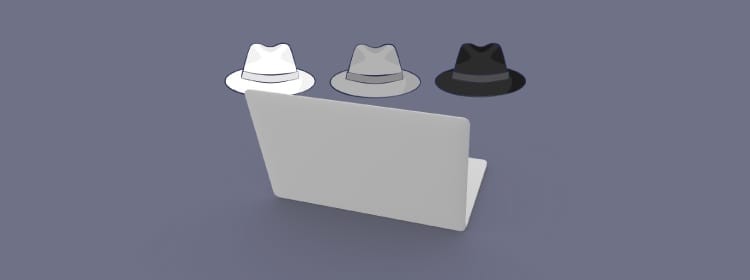
Types of Hackers-
- White Hat Hackers- These are the appropriate people who help us on the dark web. White hat hackers, commonly referred to as ethical hackers, are cybersecurity professionals who help the state and corporations by carrying out penetration tests and finding security holes. To defend themselves from black hat hackers and other cybercriminals, ethical hackers employ a range of strategies. They enter into our system with the goal of identifying flaws and helping you remove malware and viruses.
- Black Hat Hackers- The majority of cybercrime nowadays is committed by black hat hackers. Black hat hackers typically have financial goals in mind. These cybercriminals scan individual computers in commercial and financial systems for security holes. By taking advantage of any security flaws they discover, they can break into your network and obtain your financial, business, and personal information.
- Grey Hat Hackers- Between white hat and black hat hackers are grey hat hackers. Grey hat hackers might not exploit their expertise for self-promotion, but they are still capable of having both good and harmful motives. For instance, a hacker who infiltrates a company and discovers a vulnerability might disclose it online or notify the company. However, hackers turn into black hat hackers if they employ their hacking abilities for profit.

As you can see the importance of ethical hacking in today’s world, it is always important to remember to be on the law’s side because you nothing ever vanishes from the internet and you’ll always be found no matter how much you try to hide.

